In today's post, we will learn about Network basics for WiFi Cracking...
WLAN Basics For Wifi Cracking:
We call it a wireless local area network. This network uses to communicate without any connection. The network also uses radio and infrared to communicate. It is a kind of local area network.
We can use the network of LAN from many devices such as WiFi and Bluetooth, we can also use it by creating a connection to the LAN.
Just the security of this network has been its biggest problem.
One advantage in LAN is that we can put a password for security in it and after that, we will ask for this password whenever we run the internet from it, and after that, it will run the network.
What is a Wireless Access Point?
An Access Point is a device, such as a wireless router, that helps wireless devices connect to a network.
What is a mac address?
Mac address is known as physical address, the hardware address is 48 bits or 12 digit hexadecimal code that all networking devices have, which can be connected to the network, all have a unique 12 Digit mac address, it is inserted in their NIC card during its manufacturing and MAC address is worldwide unique.
The Mac address Format for WiFi Cracking-
It is different from all network devices, so you must have a strong mind, there are so many companies in the world that make network devices like computer, laptop, pc, router, mobile, etc., then How can mac address be unique every time?
let's know the format of mac address so that you will know why mac address is the unique
As we all know that mac address bits consist of 48 bits and in the form of hexadecimal, there are 12 digits i.e. the first 6 digits of mac address i.e. 24bits which are called OUI (organisationally unique identifier) and mac address Network interface controller is specific to the 6 digits of the last i.e. 24bits of the last.
The 24bits of First which all the vendors making network devices get by registering with IEEE.
This IEEE Registration Authority Committee provides the number of unique 24bits to all companies and the number of 24bits of Last generates by the vendor companies.
What is a man in the middle attack?
As the name of Man In Middle means MITM, a third person comes in between two people in this type of hacking.
And you can read their communication by sitting in the middle.
When the first-person is talking to the second person.
And in the middle, there is a hacker falling on their data.
The open server is used in this hacking, whenever we are running mobile internet, we are left with these things.
Because our data is directly from our mobile to the tower and then from the tower to the company through the underwater sea to the country where our request file is a host on a server and then the request takes a file from there Comes and then opens the file in our mobile through tower and tower by OFC.
Therefore, there is no expectation of a Man In Middle attack while running mobile Internet because it is not so easy to break the security of the data provider.
But do you know where I have done these middle attacks the most? Let me tell you.
Man In Middle attack is most successful in WiFi or you can say open WiFi network.
Whenever you get open WiFi, you start connecting to it and running the internet, but do you know that a hacker connected to the same network protocol can remove the information of people connected to that WiFi at the same time.
Not only that, but they can also read their messages and all they do is use a software hacking tool called "Shark wave".
Three main parts of wireless security :
1. Network Basics
2. Cracking WEP encryption
3. Cracking WPA encryption
Operating System: Kali Linux
It is an open-source platform.
There are three main encryption types:
1. WEP: Very easy to crack.
2. WPA: More challenging than WEP.
3. WPA2: Similar to WPA but uses a stronger encryption algorithm.
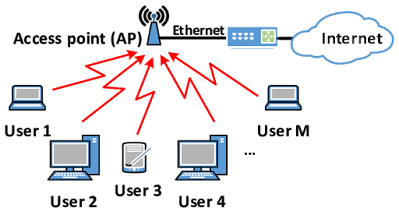
Network Basics For Wifi Cracking:
A network is a number of devices connected together.
Use: to transfer data or share resources between the connected devices.
All networks (wifi or wired) achieve this using the same principle.
One device acts as a server, the server contains the data that is shared between the connected devices
In most wi-fi networks, the server is the router, and the shared data is the internet.
Conclusion:
● The only device in the network that has access to the shared data (internet in most cases) is the server.
● All the connected devices have no direct access to the internet.
Question:
Then how come all the devices in the network can access Then how come all the devices in the network can access the internet ???
When a device in the network needs to access the shared resource (internet), It sends a request to there server (router)
The router then processes the request.
When a device in the network needs to access the shared resource (internet), It sends a request to their server (router).
● All of this data (requests and responses) is transfer as packets in wi-fi networks, these packets are sends in the air between the devices.
Question: So can we just capture all of these packets and So can we just capture all of these packets and analyze them?
Answer: Yes we can, and this is what's called sniffing.
Theory Behind WEP cracking or Wifi Cracking:
The first encryption they are going to talk about breaking is going to be the WEP security protocol because it's the oldest one.
It's the easiest one to break.
But we still need to learn how to break it because you will see networks that still use with encryption
uses an algorithm called RC4. for each packet is encrypted at the access point and then it's sent to the air.
Once the client receives it since the client has the key it will be able to decrypt the packet and read the information inside it.
So very simple the IP encrypted packet sent that client to receive it.
The client has the key so the client decrypts it.
Same way when the client says the packet is encrypted and then sends it in the air the access point to receive it.
The access point has the key so it'll decrypt the packets.
So each packet sent into the air has a unique keystream.
Which ensures that the keystream is unique by using a 24-bit initialization vector.
An initialization vector is a random number it's send into each packet and into plaintext.
So this part is not encrypted.
If you read the packet you'll be able to read it in plain text.
The problem with the IP or the initialization vector it's very short the 24 bits are not that long.
So in a busy network, there will be a very large number of packets sends into the air.
This means the number of possibilities of random IPs will be exhaust.
What Next for Wifi Cracking?
So the initialization vector is a 24 bit random keep it sent into the air in each packet and it's sent into plaintext as the plaintext in a busy network.
We're going to have a very large number of packets.
This means that the possibilities of unique IPs will be exhausted and that we will who are sniffing these all these packets who will be able to collect two packets that have the same initialization vector.
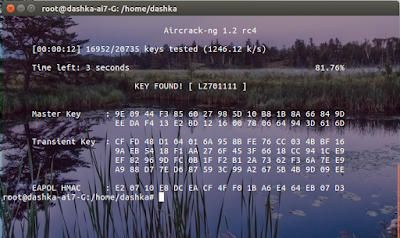
Once we have two packets they have the same initialization vector aircraft energy that can use statistical attacks to determine the keystream.
And after that, it will be able to determine the work.
So from the above, we know the more initialization vectors that we collect the more likely that will successfully crack the whip.
So our main goal now when we try to crack WEP is to collect as much as we can.
Because once we have a large number of IPs and we're going to have two packets they use the same IP then aircraft ng is more likely to be able to determine the keystream.
And they were key for the target network.




Informative 😄
ReplyDeleteWe want more like this 🙌
Thank you 😊😘
DeleteWifi Cracking Network Basics For Wifi Hacking >>>>> Download Now
Delete>>>>> Download Full
Wifi Cracking Network Basics For Wifi Hacking >>>>> Download LINK
>>>>> Download Now
Wifi Cracking Network Basics For Wifi Hacking >>>>> Download Full
>>>>> Download LINK Tg
useful information.....👍✌✌✌✌
ReplyDeleteThank you 😊
Delete🔥🔥
ReplyDeleteThank you :)
Deletevstpatch.net
ReplyDeleteGlarysoft Malware Hunter Pro Crack
Xilisoft YouTube Video Converter Crack
WiFi Hacking Password Crack
Pitch n Time Pro Crack
Miracle Box Setup Tool Crack
cDock Crack
Wow, amazing block structure! How long
Have you written a blog before? Working on a blog seems easy.
The overview of your website is pretty good, not to mention what it does.
In the content!
Wifi Cracking Network Basics For Wifi Hacking >>>>> Download Now
ReplyDelete>>>>> Download Full
Wifi Cracking Network Basics For Wifi Hacking >>>>> Download LINK
>>>>> Download Now
Wifi Cracking Network Basics For Wifi Hacking >>>>> Download Full
>>>>> Download LINK Mk
Post a Comment